By
Raditio Ghifiardi
Africa-Press – Eritrea. The Spark
“Why keep buying the future when we can invent it ourselves?”
That question wouldn’t leave me alone.
Every day inside Security Operations Centers (SOCs) across Southeast Asia I saw the same drama: tens of thousands of alarms, too few analysts, and attackers who never sleep. Commercial tools—powerful as they were—felt like sealed black boxes shipped from far away, priced in foreign currency, and tuned for somebody else’s traffic patterns.
Indonesia deserved better.
So a small team and I set out to build a cyber-defence platform that speaks our language, fits our budgets, and grows with our talent. We called it ADA—the Anomaly Detection Agent—and centred it on one conviction:
Many small, specialist AIs working together beat one giant, mysterious AI.
A Hospital in the Cloud
To make that idea concrete, we borrowed the structure of a hospital. No single doctor handles everything; surgeons, radiologists, nurses and pharmacists coordinate through shared charts.
ADA copies that playbook—only the “staff” are software agents.
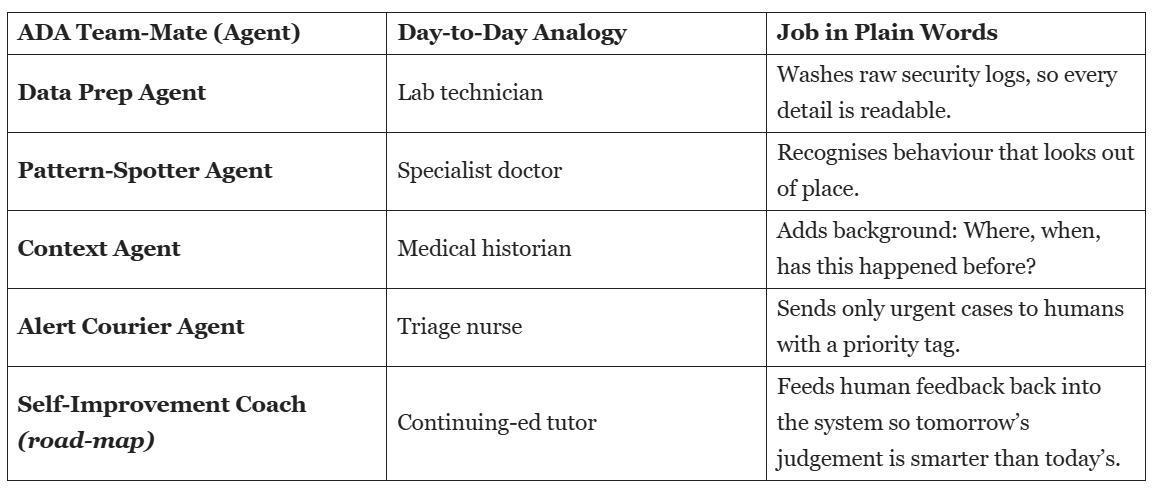
These agents connect through an orchestration network we call LangGraph—imagine an interactive flow-chart where each node is a tiny expert and the arrows show who talks to whom. Because every role is modular, we can swap or upgrade one without disturbing the rest—just like replacing a stethoscope with a smarter model.
A Cloud Built for the Nation
Indonesia’s digital economy now lives mostly in the cloud, so ADA meets it there, scanning new log entries every few minutes instead of every few hours. Yet early on we hit a bottleneck: our first cloud database made deep searches slow and expensive.
The Migration Breakthrough
We decided to shift the heavy data to a high-speed warehouse designed for lightning-fast analytics. To avoid downtime we used a “dual-write” move—writing to both the old and the new store until we were sure nothing went missing. Overnight:
Search time fell from minutes to seconds.
Cost per query dropped sharply.
All evidence sat in one tidy, searchable archive instead of scattered folders.
Think of it as moving from a cluttered desk drawer to a labelled filing cabinet—same papers, but far easier to find.
How ADA Learns on Its Own
Automatic Sensitivity Control
– When false alarms climb, ADA quietly tightens its criteria; if threats slip through, it relaxes them.
Regular Self-Improvement Cycle
– Once a week it reviews newly labelled examples and updates its internal “muscle memory,” no midnight guru required.
Clear “Why” Notes
– Every alert carries a short explanation—“Unusual login time,” “Past risky IP”—so even a finance officer can grasp the decision.
The result? Less noise, more true threats caught, and a system that gets sharper the longer it runs—like a child who studies yesterday’s mistakes and returns wiser.
Why This Matters Beyond Tech
a. Digital Sovereignty
Owning our own security tools means owning our data destiny. ADA proves Indonesia can craft world-class AI instead of renting it.
b. Talent Magnet
Students in Jogja or Makassar often assume cutting-edge AI only comes from California. ADA shows they can code something that protects banks, hospitals and even government networks.
c. Blueprint for the Global South
Many nations face the same budget and talent gaps. Because ADA’s design is open and modular, others can copy, adapt or extend it—turning one country’s win into a regional shield.
Stories from the Field
Telecom Pilot – After deployment, a major telecom cut false alarms by 35 % in two weeks. Analysts now spend their day on real incidents, not noise.
University Hackathon – Three undergrads wrote a new “phishing detector” agent in 48 hours and plugged it into ADA without touching core code.
Regional SOC Collaboration – Once everything lived in the high-speed warehouse, cross-border sharing of anonymised threat data became as easy as sending a link.
Each success reinforces a simple rule: open architecture lets local innovation scale.
Lessons Anyone Can Borrow
Start with a Pain People Feel – “Too many alerts” was obvious to every stakeholder.
Think in Lego Bricks, Not Monoliths – Easier to test, replace and explain.
Show Human Impact First – Dashboards that count “hours of analyst fatigue saved” speak louder than percentages.
Plan for Tomorrow’s Data, Not Today’s – The warehouse move taught us to think five years ahead.
Invite Feedback Early – Security teams trust tools they help shape.
The Road Ahead
Always-Verify Security Model – Soon ADA won’t just warn; it will block suspicious traffic in real-time.
Community Editions – Lightweight packages for schools and small businesses.
Open Practice Sets – Anonymised Indonesian cyber-datasets for students and researchers worldwide.
The dream? Indonesia becomes a global reference point for ethical, people-first AI in cybersecurity.
A Call to Indonesia’s Youth
Close your eyes and picture 2030:
Indonesian-built AI shields Southeast Asia’s smart cities.
High-school hackathons teach agent-based design as a core skill.
Jakarta hosts the annual “Global South Cyber-AI Summit.”
That future needs coders, storytellers, policy-makers and teachers—anyone willing to learn and lead. You don’t have to memorise every algorithm; start by understanding a problem your community experiences and plug into a modular ecosystem like ADA.
Build local. Share global. Own the narrative.
Final Thought
I began with a question; let me end with a challenge:
“If a handful of Indonesian engineers can build ADA, what could millions of inspired Indonesians create together?”
Let’s find out.
moderndiplomacy
For More News And Analysis About Eritrea Follow Africa-Press







